Installing Bytemark Symbiosis on Debian 9 (Stretch)

Start with the network install or “netinst” image to install the operating system. This image contains just the minimal amount of software to start the installation and fetch the remaining packages over the internet. I’m using the 64…
Read more »Sending Symbiosis backups to a server outside Bytemark

Symbiosis is an easy to use hosting environment developed by Bytemark. The system includes backup2l to handle backups. backup2l is a lightweight command line tool for generating, maintaining and restoring backups. The backup2l configuration is generated from the…
Read more »How to prevent web page caching across all browsers
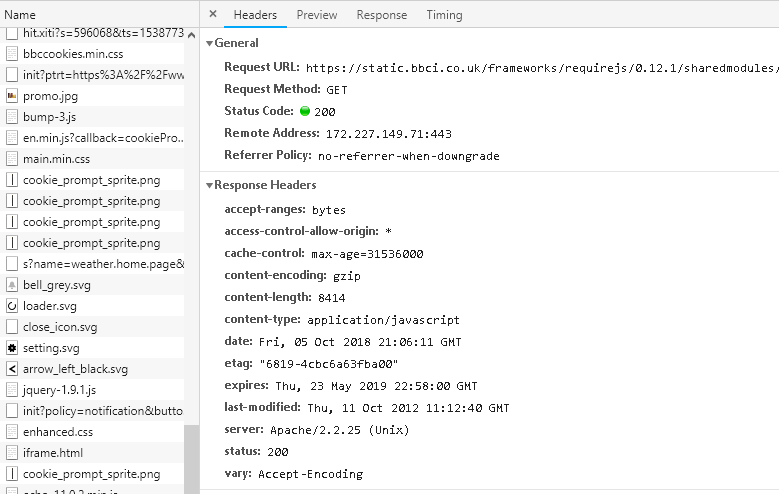
There are two main types of cache headers, Cache-Control and Expires . They define the caching characteristics of your resources. Typically, Cache-Control is a better approach than Expires , however, both headers can be used simultaneously. Cache headers are applied…
Read more »Deleting directories/files with paths too long for Windows delete
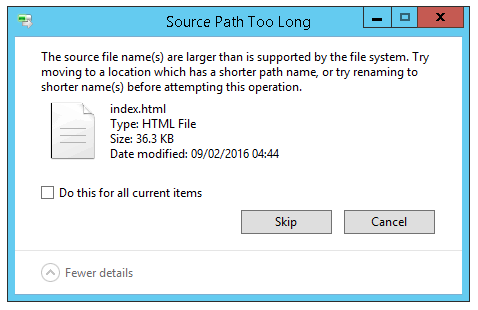
In Windows API the maximum length for a path is defined by MAX_PATH which is 260 characters. A local path is structured using drive letter, colon, backslash and folder names separated by backslashes, followed by a null terminator.…
Read more »Using .htaccess to redirect a .co.uk domain to .com for all pages

Customers often register .co.uk , .com and .uk domains to protect their brand. Domains can be left dormant or configured to redirect to the active site. A redirect is useful if visitors try to guess your top level domain…
Read more »Unable to enter password at the disk decryption splash screen (Surface Pro)
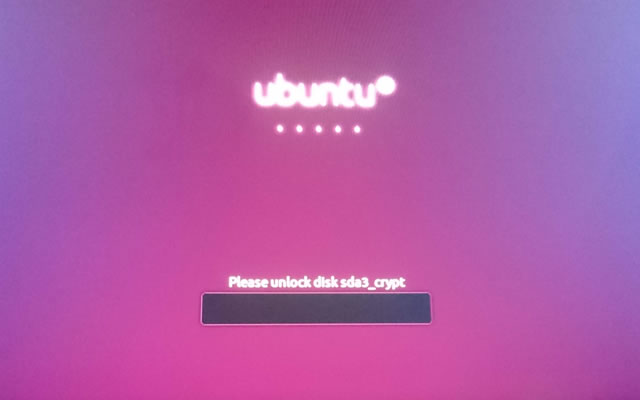
Ubuntu 18.04 LTS is a good choice for Linux on the Surface Pro 3 if you decide to replace Windows. Without disk encryption the installation process took about 20 minutes without any patches. With disk encryption I was…
Read more »How to convert a virtual hard disk file (VHDX to VHD)

If you have the Hyper-V role installed you can convert a virtual hard disk file using PowerShell or the GUI. Why would you do this? You are moving to a new server which requires the old format You…
Read more »Using a U2F Yubikey with Linux Mint 19 Tara

Universal 2nd Factor (U2F) is an open authentication standard that strengthens and simplifies two factor authentication (2FA) using USB or NFC devices. It enables internet users to securely access any number of online services using a single security…
Read more »How to copy data over SSH with secure copy (scp)

scp or secure copy is a command used for sending files over SSH. You can copy files between computers, say, from your local PC to a server or vice versa. It’s a very secure method of copying files…
Read more »How do I copy file names starting with a dot in Linux?

UNIX / Linux file systems do not have a hidden file attribute. A file or folder is typically hidden by using a period as the first character in the file name i.e. .hiddenfile . In order to list all files…
Read more »